This post will tell you how to create a Certificate Authority (CA) signed SSL certificate for a Droplet hosted on DigitalOcean with its own domain name. This assumes you own a domain name and have it pointing to an Ubuntu server.
Let’s Encrypt provides signed SSL certificates for free as long as their site can verify that you do manage a domain name. They do it by having you make a few temporary entries to the DNS records pertaining to the domain name that they can match to the machine making the request. This is how it is done.
Install the client (the official Let’s Encrypt ACME client)
sudo add-apt-repository ppa:certbot/certbot sudo apt-get update sudo apt-get install certbot
Create the request for the wildcard certificate. Let’s say you own example.com. Your certificate will be valid for any subdomains of that, such as www.example.com, mail.example.com, etc., but not simply example.com. For that you’ll need to add an extra term in the request, and add a second entry to your DNS records for Let’s Encrypt. Execute the following command, enter ‘Y’ to have your IP logged, but do not hit enter until after adding the entries, in the next step.
sudo certbot certonly --server https://acme-v02.api.letsencrypt.org/directory --agree-tos --manual --preferred-challenges dns -d example.com -d *.example.com
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator manual, Installer None Obtaining a new certificate Performing the following challenges: dns-01 challenge for example.com dns-01 challenge for example.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - NOTE: The IP of this machine will be publicly logged as having requested this certificate. If you're running certbot in manual mode on a machine that is not your server, please ensure you're okay with that. Are you OK with your IP being logged? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please deploy a DNS TXT record under the name _acme-challenge.example.com with the following value: yvKpslex2Qxd5G8altPOv2K_dfTBgIxNEiwVFXD_Ex8 Before continuing, verify the record is deployed. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Press Enter to Continue
Go to your DigitalOcean Networking panel and access the records for example.com add a TXT entry with the specifics provided by the certbot client (sample shown above). You’ll need to paste the long string of gibberish into the VALUE field and type _acme-challenge into the HOSTNAME. Note, do not type the .example.com domain ending, as it is added automatically on DigitalOcean (and many other providers).
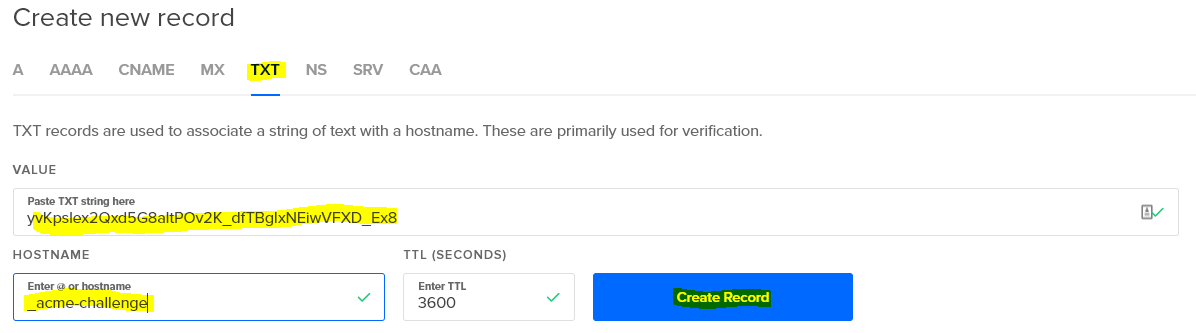
Now go back and hit Enter in your certbot client. You’ll have to do this twice, once for example.com, and once for *.example.com. Once done, you’ll see something like the following, which will tell you how to renew your certificates in ninety days, when they expire (but they’re free, and it’s literally a one line command to renew them).
IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/example.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/example.com/privkey.pem Your cert will expire on 2019-01-17. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
You may now delete those TXT entries in the DNS records. Your certificates are in a non-standard place, not /etc/ssl/cert and /etc/ssl/private, so be sure to update your Apache or Nginx configuration files accordingly.
An interesting topic and I’m glad to come across your page where I found some helpful insights. Check out my website Article Star too, if you need additional resources about Social Media Marketing.
Your site visitors, especially me appreciate the time and effort you have spent to put this information together. Here is my website QU9 for something more enlightening posts about Membership Websites.
Hey, if you are looking for more resources, check out my website QH3 as I cover topics about Car Purchase. By the way, you have impressive design and layout, plus interesting content, you deserve a high five!
I like the comprehensive information you provide in your blog. The topic is kinda complex but I’d have to say you nailed it! Look into my page 92N for content about Thai-Massage.
I am genuinely thankful to the owner of this website for sharing his brilliant ideas. I can see how much you’ve helped everybody who comes across your page. By the way, here is my webpage FQ6 about Airport Transfer.
You rocked this subject and have astounding insights. I also work hard in putting together great content about Thai-Massage, feel free to visit UY5
Thank you for sharing your precious knowledge. Just the right information I needed. By the way, check out my website at UQ4 about Podcasting.